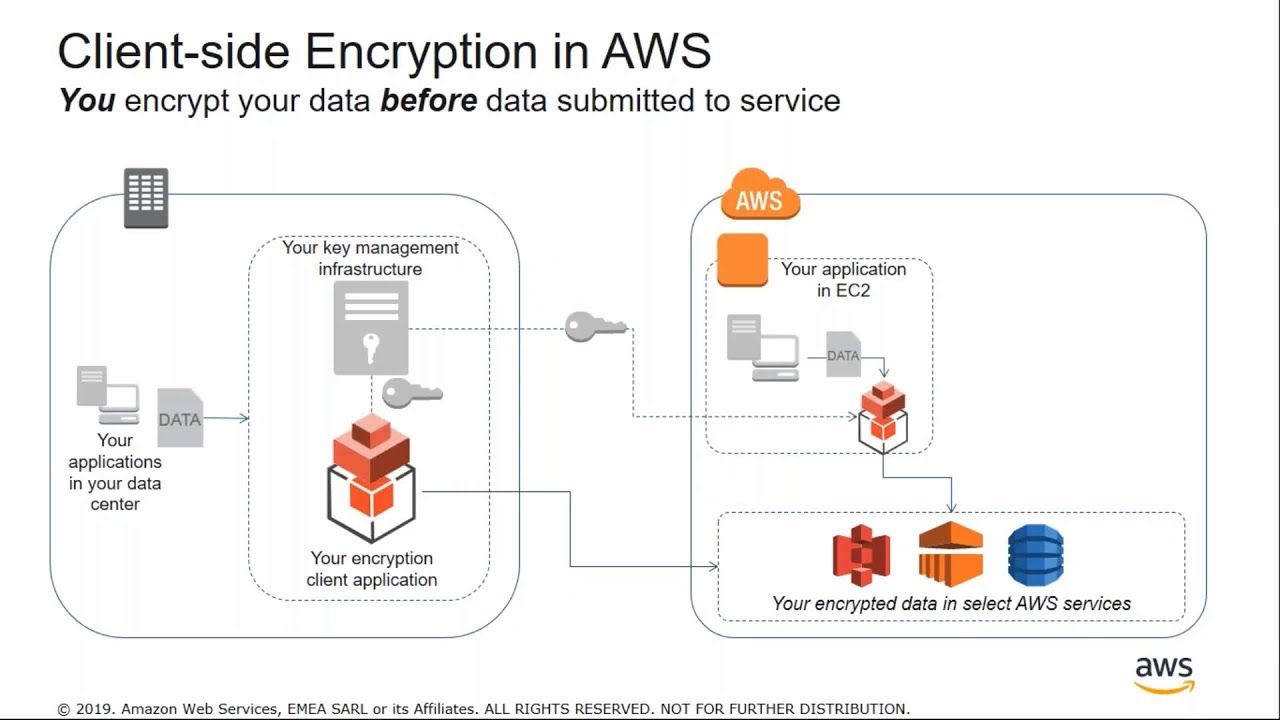
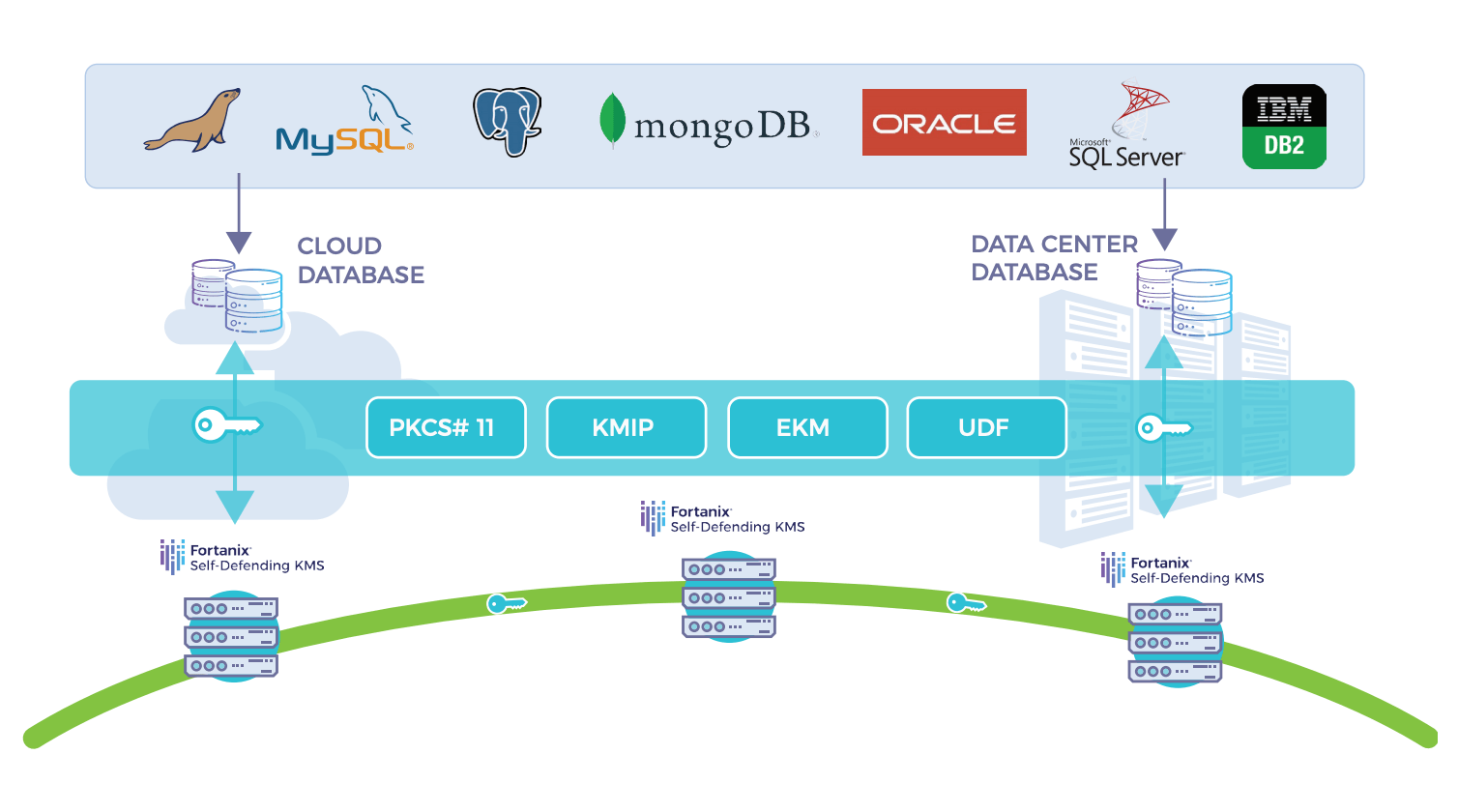
Network Encryption: A Double-edged Sword for Cybersecurity | Data Center Knowledge | News and analysis for the data center industry
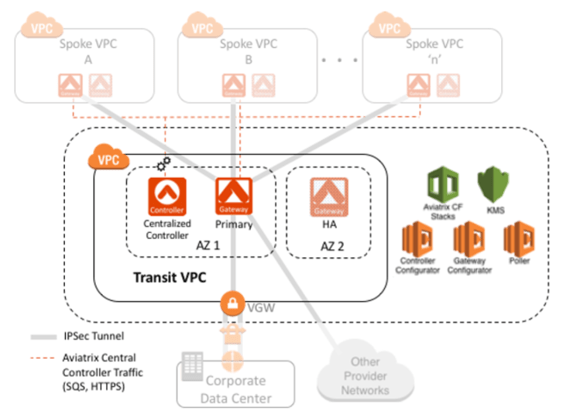
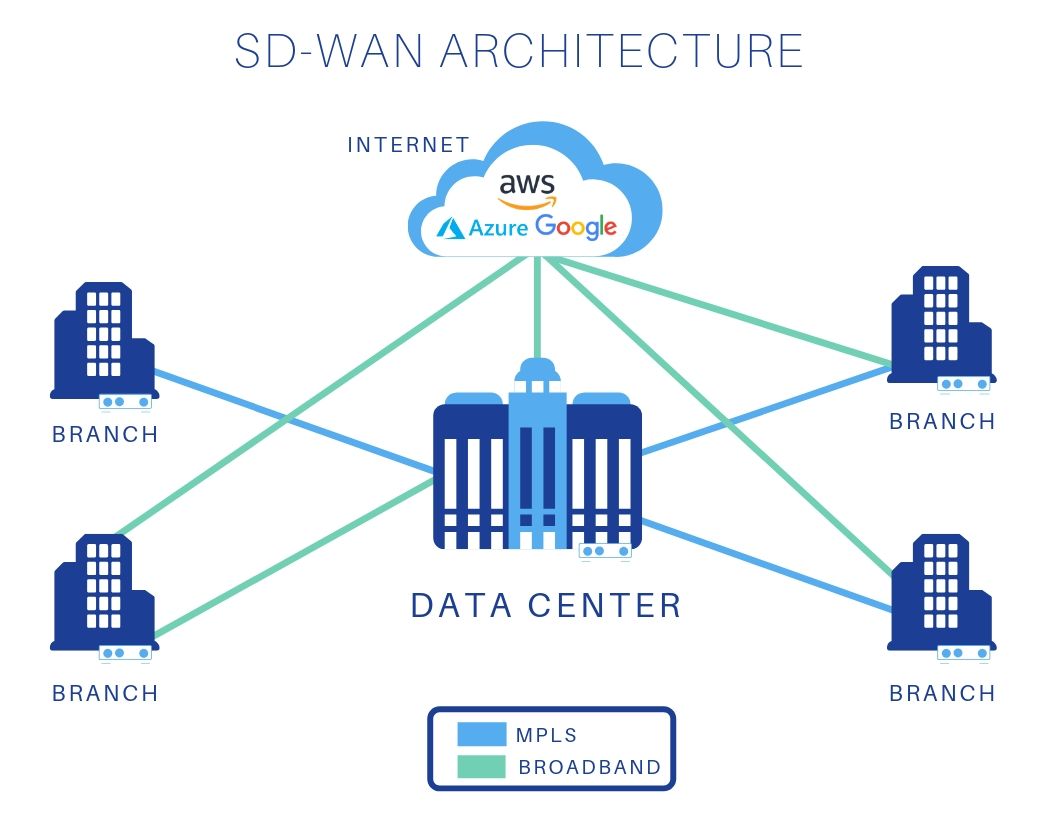
How should I encrypt data-in-motion between my data center and the AWS Global Transit VPC? - Aviatrix

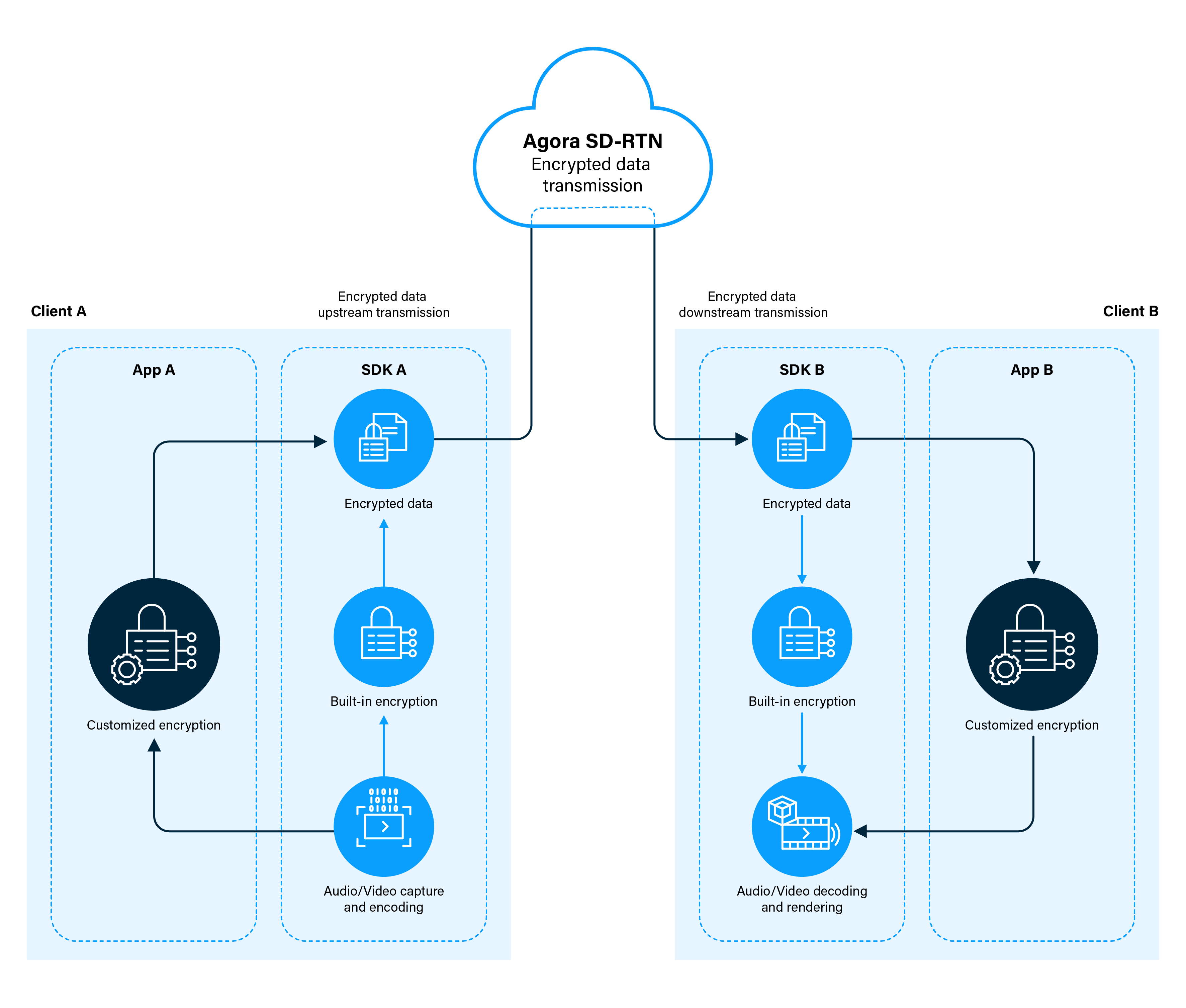
Google Boosting Encryption Between Data Centers | Data Center Knowledge | News and analysis for the data center industry

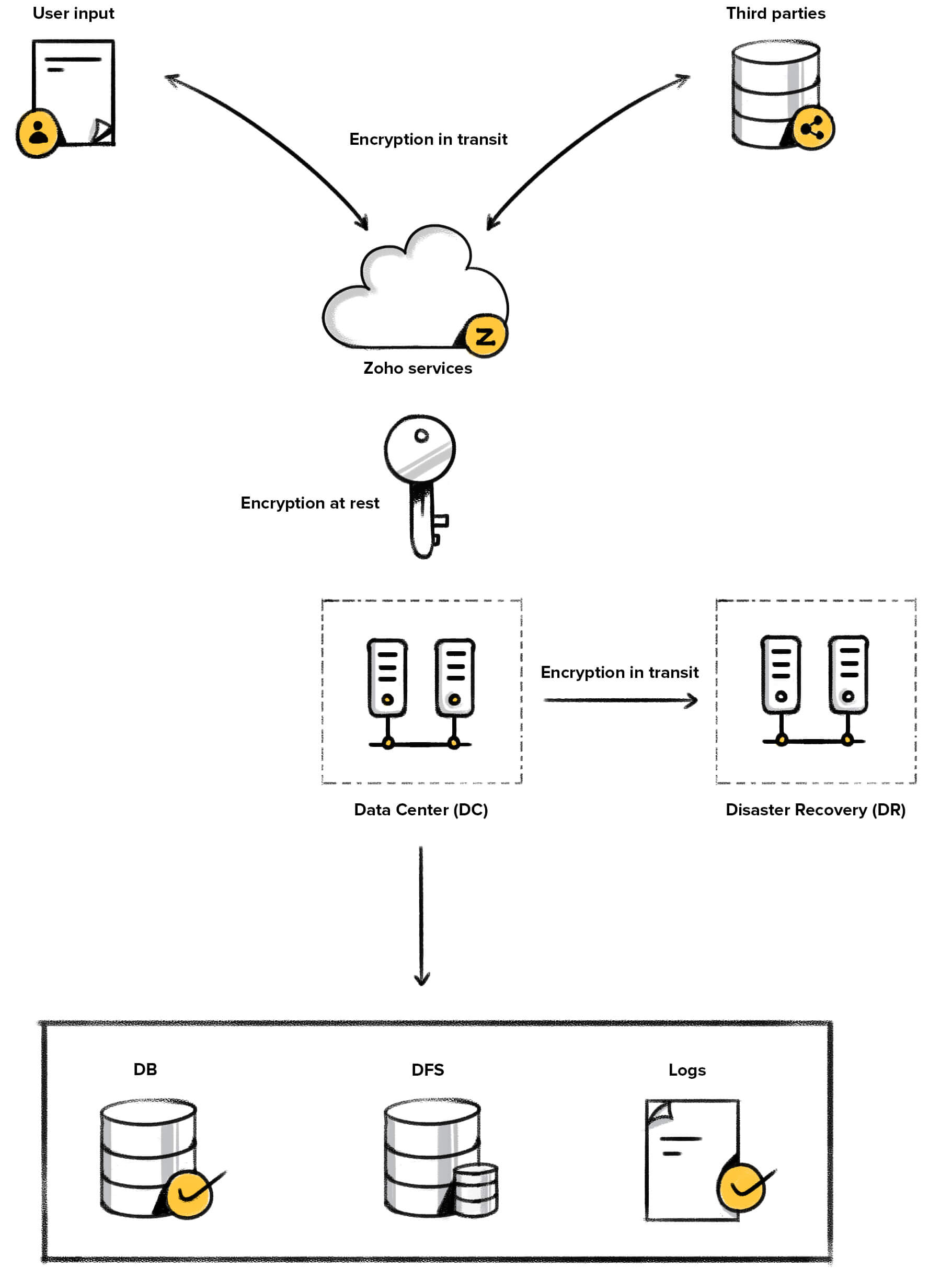
What Is Data Center Security? 6 Ways to Ensure Your Interests Are Protected - Hashed Out by The SSL Store™

Are Encrypted Lockboxes for Data Centers Worth the Usability Cost? | Data Center Knowledge | News and analysis for the data center industry

Equinix Pitches Single System for All Your Cloud Encryption Keys | Data Center Knowledge | News and analysis for the data center industry